Identity Providers
In addition to authentication with Windows credentials and email/password, Qalyptus supports SSO authentication with SAML 2 using Identity Providers (Okta, Auth0, etc.) and JWT.
The four authentication methods that Qalyptus Server offers are supported in our Qlik Sense extensions: Qalyptus On-demand, Qalyptus Self-Reporting, and Qalyptus Notify.
You can configure multiple Identity Providers.
Configure a SAML Identity Provider
Create a SAML Identity Provider
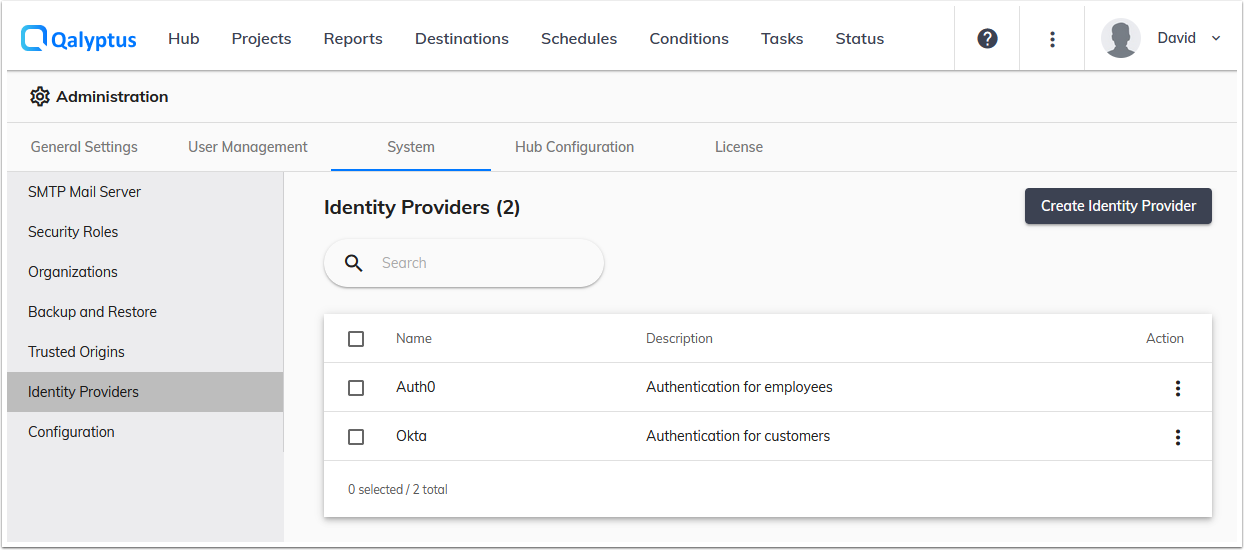
To create a new SAML Identity Provider, do the following:
- Connect to Qalyptus Server as an administrator
- Go to Qalyptus Administration > System > Identity Providers
- Click Create Identity Provider
- Enter a Name
- Enter a description (optional)
- Select the Type SAML
- Check the option Sign Auth Request If you want to sign the Authentication request and if it's supported by your IdP
- Use the metadata file or the information below in your Identity Provider Settings.
- Assertion Consumer Service(ACS) URL
- Service Provider(SP) Entity ID The metadata file contains all the information about the Service Provider (Qalyptus). Qalyptus automatically retrieves the Identity Provider certificates.
- Enter the Entity ID provided by your IdP (Issuer URL)
- Enter Singl Sign-On URL (SSO URL) provided by your IdP
- Enter the Button label. Example: Log in with Okta
- Click Save
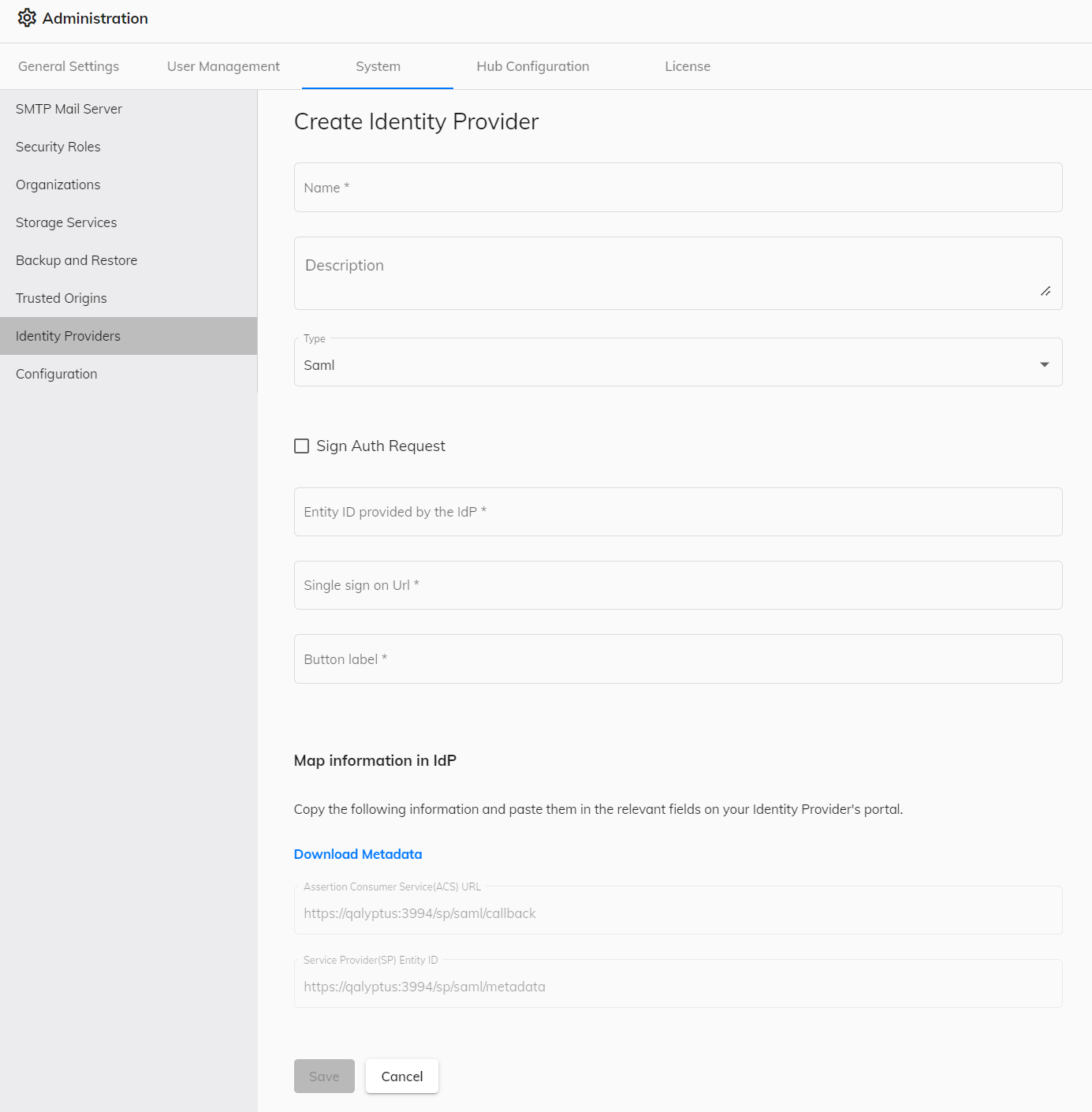
If your IDP is Ping Identity, add the attribute Email Address with the value email in the Application settings.
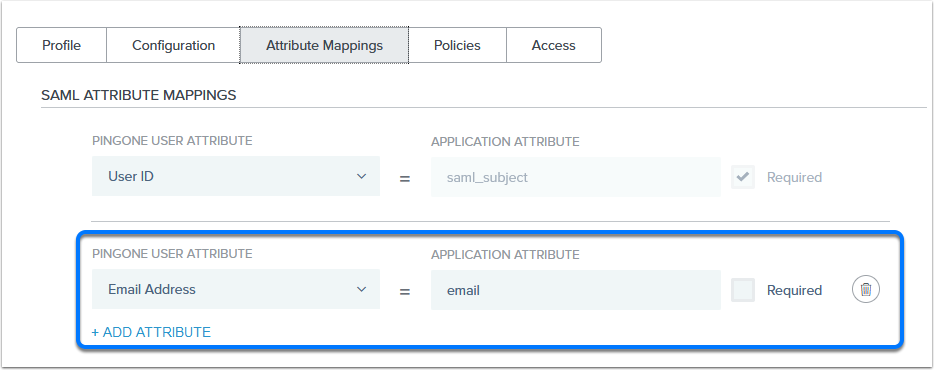
Use a SAML Identity Provider
A SAML Identity provider must be added to an organization. Only the members (users) of the organization can use the specific Identity provider.
You can add more than one Identity provider to an organization. The member of the organization will see a Log in button for each Identity Provider.
If an organization uses only one Identity Provider, the user is automatically redirected to authenticate (the login button is not displayed).
Login Page
Qalyptus On-Demand authentication settings
Configure a JWT Identity Provider
Create a JWT Identity Provider
To create a new JWT Identity Provider, do the following:
- Connect to Qalyptus Server as an administrator
- Go to Qalyptus Administration > System > Identity Providers
- Click Create Identity Provider
- Enter a Name
- Enter a description (optional)
- Select the Type JWT
- Enter a Certificate public key. You can use OpenSSL to generate the private and public keys. Enter the public key and store the private key in a secure location
- The JWT attributes is the JWT Payload format to have in the JWT token.
- Click Save
:::tipGenerate private and public keys Open a terminal window and use OpenSSL to generate public and private keys. Store the private key in a secure place. The public key is used in the IDP configuration.
First, download OpenSSSL from the official website;
Then, run the following two command lines. you can change the day parameter.
openssl genrsa -out privatekey.pem 4096
openssl req -new -x509 -key privatekey.pem -out publickey.cer -days 1825
Finally, open the generated .pem files with a text editor. :::
You can only create one JWT identity provider in Qalyptus Server. A JWT Identity Provider is not assigned to an organization.
Qalyptus only supports the encryption algorithms: RS256, RS384 and RS512.
Use a JWT Identity Provider
The JWT Identity Provider created in Qalyptus Server is used to authenticate a user with a JWT token. The token is created by the following:
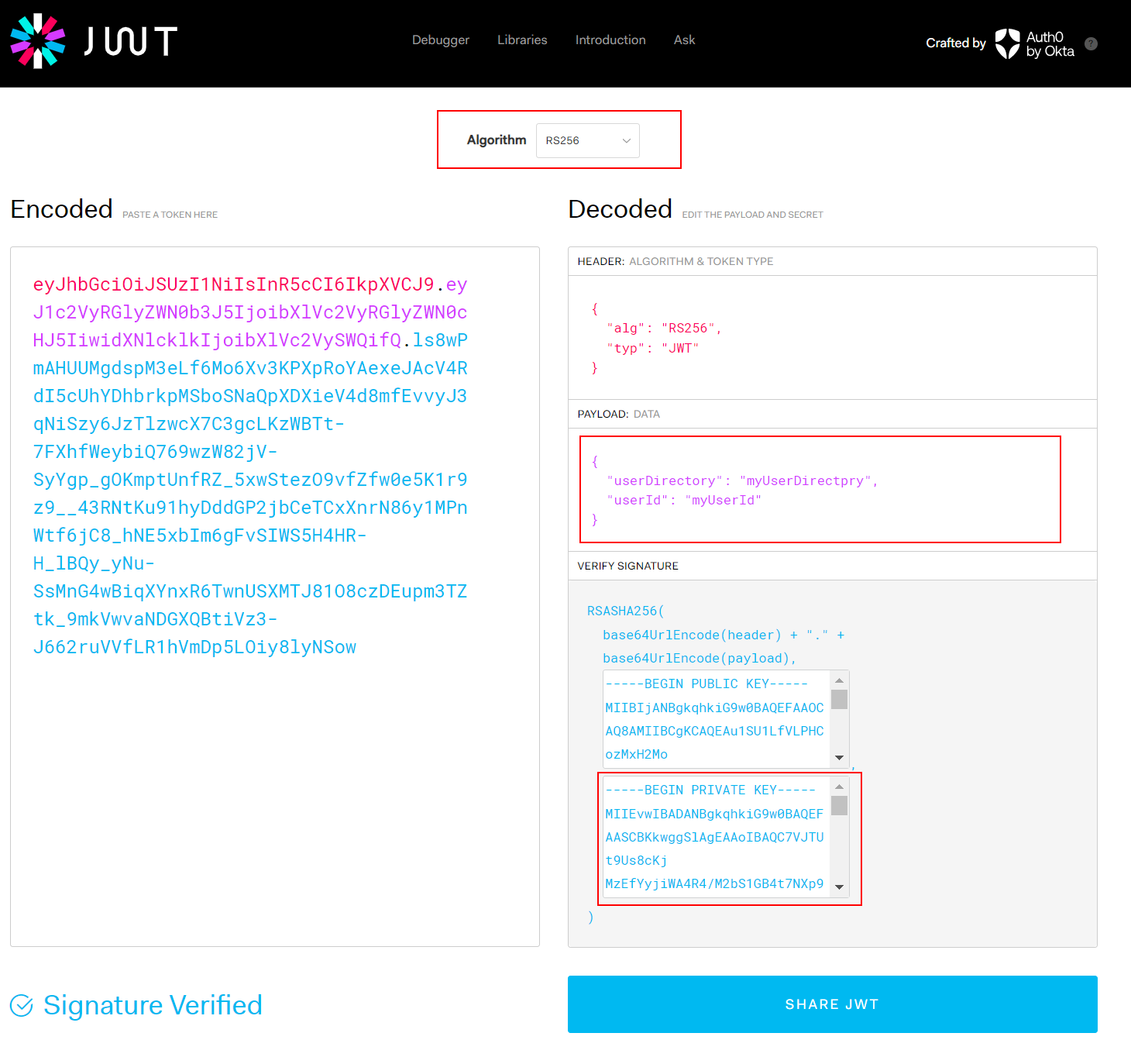
- The Playload must contain the user info using the attributes userId and userDirectory. The userId and userDirectory must be the same as the user in Qlik Sense.
- Use one of the following encryption algorithms: RS256, RS384 or RS512.
- Sign the JWT token with the private key generated with the public key used in the JWT Identity Provider configuration.
You can use diffrent programing languages to sign the JWT token.
An example of a test JWT token created using the jwt.io website is.
Log in with the JWT token
Use the Qalyptus Server API to authenticate a user. The Endpoint to use is GET /api/v1/login/jwt-session.
The user agent must send the JWT token, created previously, in the Authorization header using the Bearer schema.
Visit the API documentation to learn more.
You can use the JWT authentication method to authenticate users using Qalyptus On-Demand, Qalyptus Self-Reporting, or Qalyptus Notify in a Qlik Sense app or embedded analytics.